設定例
IPsecを使って2つのLANを接続する設定(Aggressiveモード)
全機種対応
説明
ローカルネットワークユーザ間をIPsecで接続するための設定です。
アドレスが未確定のルータよりIPsec通信を開始する必要があります。
アドレスが未確定のルータよりIPsec通信を開始する必要があります。
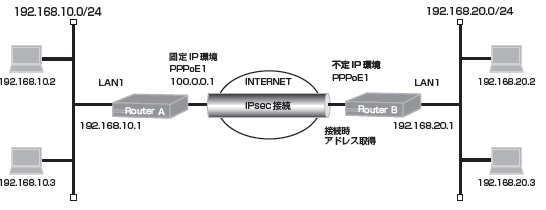
構成
コマンド設定
Router A
hostname Router_A interface ewan 1 ip address 100.0.0.1 255.255.255.0 exit interface lan 1 ip address 192.168.10.1 255.255.255.0 exit vpn enable vpnlog enable interface ipsecif 1 crypto map Router_B exit crypto isakmp policy 1 authentication prekey group 5 hash sha key ascii secret1 peer-identity host Router_B exit crypto map Router_B 1 match address 1 set peer host Router_B set pfs group5 set transform-set aes256-sha exit ipsec access-list 1 ipsec ip 192.168.10.0 0.0.0.255 192.168.20.0 0.0.0.255 ipsec transform-set aes256-sha esp-aes-256 esp-sha-hmac ip route 200.0.0.1 255.255.255.255 100.0.0.254 ip route 192.168.20.0 255.255.255.0 connected ipsecif 1 end
Router B
hostname Router_B interface pppoe 1 ip nat inside source list 1 pool global_IP pppoe server internet pppoe account ********@***.***.ne.jp ****** pppoe type host exit interface lan 1 ip address 192.168.20.1 255.255.255.0 exit vpn enable vpnlog enable interface ipsecif 1 crypto map Router_A exit crypto isakmp policy 1 authentication prekey group 5 hash sha key ascii secret1 negotiation-mode aggressive my-identity Router_B peer-identity address 100.0.0.1 exit crypto map Router_A 1 match address 1 set peer address 100.0.0.1 set pfs group5 set transform-set aes256-sha exit ipsec access-list 1 ipsec ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255 ipsec transform-set aes256-sha esp-aes-256 esp-sha-hmac ip route 100.0.0.1 255.255.255.255 pppoe 1 ip route 192.168.10.0 255.255.255.0 connected ipsecif 1 end
設定手順
Router A
| 設定内容 | 画面表示例 |
|---|---|
|
特権ユーザモードへの移行 パスワードの入力 設定情報の初期化 設定モードの変更 設定入力 設定保存 装置再起動 |
Router>enable Enter password: Router# Router#clear working.cfg Router# Router#configure terminal Router(config)#hostname Router_A Router_A(config)#interface ewan 1 Router_A(config-if ewan 1)# ip address 100.0.0.1 255.255.255.0 Router_A(config-if ewan 1)#exit Router_A(config)#interface lan 1 Router_A(config-if lan 1)# ip address 192.168.10.1 255.255.255.0 Router_A(config-if lan 1)#exit Router_A(config)#vpn enable Router_A(config)#vpnlog enable Router_A(config)#interface ipsecif 1 Router_A(config-if ipsecif 1)# crypto map Router_B Router_A(config-if ipsecif 1)#exit Router_A(config)#crypto isakmp policy 1 Router_A(config-isakmp)# authentication prekey Router_A(config-isakmp)# group 5 Router_A(config-isakmp)# hash sha Router_A(config-isakmp)# key ascii secret1 Router_A(config-isakmp)# peer-identity host Router_B Router_A(config-isakmp)#exit Router_A(config)#crypto map Router_B 1 Router_A(config-crypto-map)# match address 1 Router_A(config-crypto-map)# set peer host Router_B Router_A(config-crypto-map)# set pfs group5 Router_A(config-crypto-map)# set transform-set aes256-sha Router_A(config-crypto-map)#exit Router_A(config)#@ipsec ip 192.168.10.0 0.0.0.255 192.168.20.0 0.0.0.255 Router_A(config)#ipsec transform-set aes256-sha esp-aes-256 esp-sha-hmac Router_A(config)#ip route 200.0.0.1 255.255.255.255 100.0.0.254 Router_A(config)#ip route 192.168.20.0 255.255.255.0 connected ipsecif 1 Router_A(config)# Router_A(config)#end Router_A# Router_A#save SIDE-A % saving working-config % finished saving Router_A#reset Going to reset with SIDE-A.frm and SIDE-A.cfg. Boot-back not scheduled for next boot. Next rebooting firmware SIDE-A.frm is fine. Are you OK to cold start?(y/n)y |
※:Router Bの設定手順も同様です。
設定状態の確認
データ通信にてIPSECが確立することを確認します。
例:Router_Bより ping 192.168.10.1 source-interface lan 1を実施します。
| 確認内容 | 画面表示例 |
|---|---|
|
ping を実行する ping 応答あり |
Router_B#ping 192.168.10.1 source-interface lan 1 Sending 5, 100-byte ICMP Echos to 192.168.10.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 0/2/10 ms |
Router AのVPNログ情報を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
ログ情報の表示 vpn enable 状態 isakmp 確立状態 ipsec 確立状態 |
Router_A#show vpnlog 0000 0000:00:00.00 2011/06/17 (fri) 13:35:49 0 00000000 4dd37c80 #BOOT[V01.04(00)-053111] SIDE-A.frm SIDE-A.cfg 0001 0000:00:02.19 2011/06/17 (fri) 13:35:54 16 10000002 00000000 vpn enabled. 0002 0000:02:01.08 2011/06/17 (fri) 13:37:53 16 10000320 00000000 IKE SA<R> 1/- 200.0.0.1 0003 0000:02:01.08 2011/06/17 (fri) 13:37:53 16 10000320 00000000 7aa8cb6119000000 3b5dd3004a000000 Router_B 0004 0000:02:01.08 2011/06/17 (fri) 13:37:53 16 100003a7 00000000 Recv INIT IKE SA 1/- 200.0.0.1 0005 0000:02:01.08 2011/06/17 (fri) 13:37:53 16 100003a7 00000000 7aa8cb6119000000 3b5dd3004a000000 Router_B 0006 0000:02:01.09 2011/06/17 (fri) 13:37:53 16 10000220 00000000 IPSEC SA<R> 1/1 200.0.0.1 0007 0000:02:01.09 2011/06/17 (fri) 13:37:53 16 10000220 00000000 0d3ecdcf 318292a7 |
Router AのPhase1 SAの情報を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
Phase1 SA の情報を表示 接続状態 |
Router_A#show crypto isakmp sa ISAKMP SA current sa : 1 [ 1] 200.0.0.1 Router_B <--> 100.0.0.1 <R> Aggressive Mode UP pre-shared key DES SHA Lifetime : 1000secs Current : 52secs,1kbytes mcfg config-mode: off mcfg addr: off mcfg apl-version: IKE Keepalive: dpd ICMP Keepalive: off release on addr-change: off |
Router AのPhase2 SAの情報を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
Phase2 SA の情報を表示 接続状態 |
Router_A#show crypto ipsec sa IPSEC SA current insa : 1 current outsa : 1 [ 1] 192.168.20.0,255.255.255.0 ALL ALL <--> 192.168.10.0,255.255.255.0 ALL ALL peer: 200.0.0.1 Router_B <R> UP ESP AES(256bits) HMAC-SHA PFS:on(group5) Lifetime: 600secs Anti-Replay: Enable O-SPI: 0x0d3ecdcf Current: 63secs,1kbytes out packet : 5 error packet : 0 I-SPI: 0x318292a7 Current: 63secs,1kbytes in packet : 5 auth packet : 5 decrypt packet : 5 discard packet : 0 replay packet : 0 auth error packet : 0 |
Router Aのルーティング情報を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
ルーティング情報を表示 IPSECIF1 の経路確認 |
Router_A#show ip route Max entry: 10000 (Commonness in IPv4 and IPv6) Active entry:5 (IPv4), 2 (IPv6) Peak:5 Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF B - BGP, I - IKE, U - SA-UP, D - REDUNDANCY, E - EventAction A - AutoConfig, > - selected route, * - FIB route, p - stale info. C> * 100.0.0.0/24 is directly connected, EWAN1 C> * 127.0.0.0/8 is directly connected, LOOP0 C> * 192.168.10.0/24 is directly connected, LAN S> * 192.168.20.0/24 [0/0] is directly connected, IPSECIF1 S> * 200.0.0.1/32 [1/0] via 100.0.0.254, EWAN1 |
Router BのVPNログ情報を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
ログ情報の表示 vpn enable 状態 isakmp 確立状態 ipsec 確立状態 |
Router_B#show vpnlog 0000 0000:00:00.00 2011/06/17 (fri) 13:35:49 0 00000000 4dd37c80 #BOOT[V01.04(00)-053111] SIDE-A.frm SIDE-A.cfg 0001 0000:00:02.04 2011/06/17 (fri) 13:35:53 16 10000002 00000000 vpn enabled. 0002 0000:02:03.89 2011/06/17 (fri) 13:37:55 16 10000320 00000000 IKE SA<I> 1/- 100.0.0.1 0003 0000:02:03.89 2011/06/17 (fri) 13:37:55 16 10000320 00000000 7aa8cb6119000000 3b5dd3004a000000 0004 0000:02:03.89 2011/06/17 (fri) 13:37:55 16 100003a7 00000000 Recv INIT IKE SA 1/- 100.0.0.1 0005 0000:02:03.89 2011/06/17 (fri) 13:37:55 16 100003a7 00000000 7aa8cb6119000000 3b5dd3004a000000 0006 0000:02:03.91 2011/06/17 (fri) 13:37:55 16 10000220 00000000 IPSEC SA<I> 1/1 100.0.0.1 0007 0000:02:03.91 2011/06/17 (fri) 13:37:55 16 10000220 00000000 318292a7 0d3ecdcf |
Router BのPhase1 SAの情報を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
Phase1 SA の情報を表示 接続状態 |
Router_B#show crypto isakmp sa ISAKMP SA current sa : 1 [ 1] 100.0.0.1 <--> 200.0.0.1 Router_B <R> Main Mode UP pre-shared key DES SHA Lifetime : 1000secs Current : 54secs,1kbytes mcfg config-mode: off mcfg addr: off mcfg apl-version: IKE Keepalive: dpd ICMP Keepalive: off release on addr-change: off |
Router BのPhase2 SAの情報を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
Phase2 SA の情報を表示 接続状態 |
Router_B#show crypto ipsec sa IPSEC SA current insa : 1 current outsa : 1 [ 1] 192.168.10.0,255.255.255.0 ALL ALL <--> 192.168.20.0,255.255.255.0 ALL ALL peer: 100.0.0.1 <I> UP ESP AES(256bits) HMAC-SHA PFS:on(group5) Lifetime: 600secs Anti-Replay: Enable O-SPI: 0x318292a7 Current: 65secs,1kbytes out packet : 5 error packet : 0 I-SPI: 0x0d3ecdcf Current: 65secs,1kbytes in packet : 5 auth packet : 5 decrypt packet : 5 discard packet : 0 replay packet : 0 auth error packet : 0 |
Router Bのルーティング情報を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
ルーティング情報を表示 IPSECIF1 の経路確認 |
Router_B#show ip route Max entry: 10000 (Commonness in IPv4 and IPv6) Active entry:5 (IPv4), 2 (IPv6) Peak:5 Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF B - BGP, I - IKE, U - SA-UP, D - REDUNDANCY, E - EventAction A - AutoConfig, > - selected route, * - FIB route, p - stale info. C> * 10.0.0.1/32 is directly connected, PPPoE1 S> * 100.0.0.1/32 [1/0] is directly connected, PPPoE1 C> * 127.0.0.0/8 is directly connected, LOOP0 S> * 192.168.10.0/24 [0/0] is directly connected, IPSECIF1 C> * 192.168.20.0/24 is directly connected, LAN |
All Rights Reserved, Copyright(C) FURUKAWA ELECTRIC CO., LTD. 2011
