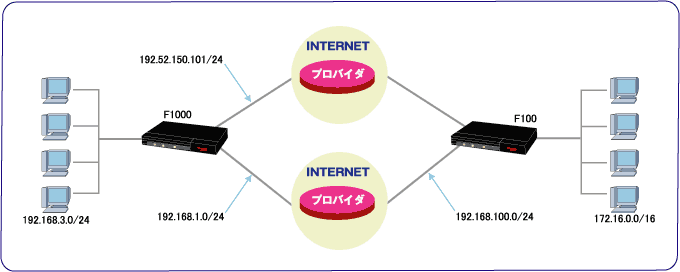
!
!
! LAN側IPアドレスを設定します。
!
Router> enable
Enter password: super ←パスワードを入力します。(実際は表示されない)
Router#
Router# configure terminal
Router(config)#
Router(config)# interface lan 1
Router(config-if lan 1)# ip address 172.16.0.1 255.255.0.0
Router(config-if lan 1)# exit
!
!
! PPPoE1インタフェース設定モードに移行します。
!
Router(config)# interface pppoe 1
Router(config-if pppoe 1)#
!
!
! PPPoEの各種設定をします。
!
Router(config-if pppoe 1)# ip nat inside source list 1 interface
Router(config-if pppoe 1)# pppoe server A-Provider
Router(config-if pppoe 1)# pppoe account user@xxxx.ne.jp secret
Router(config-if pppoe 1)# pppoe ncp both
Router(config-if pppoe 1)# pppoe auth-accept auto
Router(config-if pppoe 1)# pppoe type host
Router(config-if pppoe 1)# ip nat inside source list 1 interface
Router(config-if pppoe 1)# crypto map MultiPath_1
Router(config-if pppoe 1)# exit
!
!
! ewan 2インタフェース設定モードに移行します。
!
Router(config)# interface ewan 2
Router(config-if ewan 2)#
!
!
! 負荷分散用の設定をします。
!
Router(config-if pppoe 5)# crypto map MultiPath_2
Router(config-if pppoe 5)# ip address 192.168.100.254 255.255.255.0
Router(config-if pppoe 5)# exit
!
!
! access-listを登録します。
!
Router(config)# access-list 1 permit 172.16.0.0 0.0.255.255
!
!
! ルート情報を設定します。
!
Router(config)# ip route 192.52.150.101 255.255.255.255 pppoe 1
Router(config)# ip route 192.168.1.254 255.255.255.255 192.168.100.1
!
!
! DHCPサーバ機能を設定します。
!
Router(config)# ip dhcp pool lan1
Router(config)# default-router 0.0.0.0
!
!
! 暗号化を使用する設定します。
!
Router(config)# vpn enable
Router(config)# vpnlog enable
Router(config)# ipsec access-list 10 ipsec ip 172.16.0.0 0.0.255.255 192.168.3.0 0.0.0.255
Router(config)# ipsec access-list 64 bypass ip any any
Router(config)# crypto isakmp policy 1
Router(config-isakmp)# authentication prekey
Router(config-isakmp)# key ascii furukawa
Router(config-isakmp)# negotiation-mode aggressive
Router(config-isakmp)# my-identity kyoten1
Router(config-isakmp)# peer-identity address 192.52.150.101
Router(config-isakmp)# keepalive-icmp peer-address 192.168.3.1
Router(config-isakmp)# keepalive-icmp source-interface lan 1
Router(config-isakmp)# keepalive-icmp multi-path interface pppoe 1
Router(config-isakmp)# keepalive icmp always-send
Router(config-isakmp)# exit
Router(config)# crypto isakmp policy 2
Router(config-isakmp)# authentication prekey
Router(config-isakmp)# key ascii furukawa
Router(config-isakmp)# negotiation-mode main
Router(config-isakmp)# peer-identity address 192.168.1.254
Router(config-isakmp)# keepalive-icmp peer-address 192.168.3.1
Router(config-isakmp)# keepalive-icmp source-interface lan 1
Router(config-isakmp)# keepalive-icmp multi-path address 192.168.100.1
Router(config-isakmp)# keepalive icmp always-send
Router(config-isakmp)# exit
Router(config)#crypto map MultiPath_1 1
Router(config-crypto-map)# match address 10 multi-path
Router(config-crypto-map)# set peer address 192.52.150.101
Router(config-crypto-map)# set security-association always-up
Router(config-crypto-map)# sa-up route interface pppoe 1
Router(config-crypto-map)# exit
Router(config)#crypto map MultiPath_2 2
Router(config-crypto-map)# match address 10 multi-path
Router(config-crypto-map)# set peer address 192.168.1.254
Router(config-crypto-map)# set security-association always-up
Router(config-crypto-map)# sa-up route address 192.168.100.1
Router(config-crypto-map)# exit
Router(config)# end
Router# save SIDE-A.cfg
% saving working-config
% finished saving
|


![]()