設定例
IPsec VPNで拠点間を接続する場合の帯域制御設定
全機種対応
説明
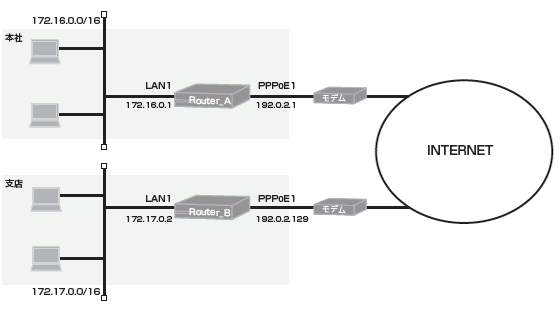
Router A(本社)とRouter B(支店)間をVPN接続し、IPsec通信を行います。
Router AとRotuer BのPPPoE1から出力されるパケットについて、以下のように帯域を確保します。
WWW通信 : 30Mbps
FTP通信 : 20Mbps
その他の通信: 50Mbps
帯域制御をおこなうとパケットの順序の入れ替わりが発生するため、anti-replay機能は無効にします。
Router AとRotuer BのPPPoE1から出力されるパケットについて、以下のように帯域を確保します。
WWW通信 : 30Mbps
FTP通信 : 20Mbps
その他の通信: 50Mbps
帯域制御をおこなうとパケットの順序の入れ替わりが発生するため、anti-replay機能は無効にします。
構成
コマンド設定
Router A
ip route 0.0.0.0 0.0.0.0 pppoe 1 ip route 172.17.0.0 255.255.0.0 connected ipsecif 1 access-list 101 permit tcp any any eq www access-list 102 permit tcp any any eq ftp access-list 102 permit tcp any any eq ftp-data vpn enable vpnlog enable ipsec access-list 1 ipsec ip 172.16.0.0 0.0.255.255 172.17.0.0 0.0.255.255 ipsec access-list 64 bypass ip any any ipsec transform-set t1 esp-null hostname Router_A interface ipsecif 1 qos output bandwidth 100M cbq qos-que cbq default-que bandwidth 50 parent root-que borrow default qos-que cbq root-que bandwidth 100 parent NULL qos-que cbq que1 bandwidth 30 parent root-que priority 3 borrow qos-que cbq que2 bandwidth 20 parent root-que priority 3 borrow service-policy output policy1 crypto map map1 exit interface lan 1 ip address 172.16.0.1 255.255.0.0 exit interface pppoe 1 ip address 192.0.2.1 ip nat inside source list 1 interface pppoe server test1 pppoe account ********@***.***.ne.jp ****** pppoe type lan exit crypto isakmp policy 1 authentication prekey encryption aes 256 hash sha key ascii furukawa lifetime 86400 my-identity kyoten1 negotiation-mode aggressive peer-identity address 192.0.2.129 exit crypto map map1 1 match address 1 set peer address 192.0.2.129 set security-association lifetime seconds 28800 set transform-set t1 anti-replay disable exit class-map class1 match ip access-group 101 exit action-map action1 set queuing que1 exit class-map class2 match ip access-group 102 exit action-map action2 set queuing que2 exit policy-map policy1 class class1 action action1 class class2 action action2 exit end
Router B
ip route 0.0.0.0 0.0.0.0 pppoe 1 ip route 172.16.0.0 255.255.0.0 connected ipsecif 1 access-list 101 permit tcp any any eq www access-list 102 permit tcp any any eq ftp access-list 102 permit tcp any any eq ftp-data vpn enable vpnlog enable ipsec access-list 1 ipsec ip 172.17.0.0 0.0.255.255 172.16.0.0 0.0.255.255 ipsec access-list 64 bypass ip any any ipsec transform-set t1 esp-null hostname Router_B interface pppoe 1 ip address 192.0.2.129 ip nat inside source list 1 interface pppoe server test1 pppoe account ********@***.***.ne.jp ****** pppoe type lan exit interface ipsecif 1 qos output bandwidth 100M cbq qos-que cbq default-que bandwidth 50 parent root-que borrow default qos-que cbq root-que bandwidth 100 parent NULL qos-que cbq que1 bandwidth 30 parent root-que priority 3 borrow qos-que cbq que2 bandwidth 20 parent root-que priority 3 borrow service-policy output policy1 crypto map map1 exit interface lan 1 ip address 172.17.0.2 255.255.255.0 exit crypto isakmp policy 1 authentication prekey encryption aes 256 hash sha key ascii furukawa lifetime 86400 negotiation-mode main peer-identity host kyoten1 exit crypto map map1 1 match address 1 set peer host kyoten1 set security-association lifetime seconds 28800 set transform-set t1 anti-replay disable exit class-map class1 match ip access-group 101 exit action-map action1 set queuing que1 exit class-map class2 match ip access-group 102 exit action-map action2 set queuing que2 exit policy-map policy1 class class1 action action1 class class2 action action2 exit end
設定手順
Router A
| 設定内容 | 画面表示例 |
|---|---|
|
特権ユーザモードへの移行 パスワードの入力 設定情報の初期化 設定モードの変更 設定入力 設定保存 装置再起動 |
Router>enable Enter password: Router# Router#clear working.cfg Router# Router#configure terminal Router(config)#ip route 0.0.0.0 0.0.0.0 pppoe 1 Router(config)#ip route 172.17.0.0 255.255.0.0 connected ipsecif 1 Router(config)#access-list 101 permit tcp any any eq telnet Router(config)#access-list 102 permit tcp any any eq www Router(config)#access-list 103 permit tcp any any eq ftp Router(config)#access-list 103 permit tcp any any eq ftp-data Router(config)#vpn enable Router(config)#vpnlog enable Router(config)#ipsec access-list 1 ipsec ip 172.16.0.0 0.0.255.255 172.17.0.0 0.0.255.255 Router(config)#ipsec access-list 64 bypass ip any any Router(config)#ipsec transform-set t1 esp-null Router(config)#hostname Router_A Router_A(config)#interface ipsecif 1 Router_A(config-if ipsecif 1)# qos output bandwidth 100M cbq Router_A(config-if ipsecif 1)# qos-que cbq default-que bandwidth 50 parent root-que borrow default※ Router_A(config-if ipsecif 1)# qos-que cbq root-que bandwidth 100 parent NULL Router_A(config-if ipsecif 1)# qos-que cbq que1 bandwidth 30 parent root-que priority 3 borrow※ Router_A(config-if ipsecif 1)# qos-que cbq que2 bandwidth 20 parent root-que priority 3 borrow※ Router_A(config-if ipsecif 1)# service-policy output high-policy Router_A(config-if ipsecif 1)# crypto map map1 Router_A(config-if ipsecif 1)#exit Router_A(config)#interface lan 1 Router_A(config-if lan 1)# ip address 172.16.0.1 255.255.0.0 Router_A(config-if lan 1)#exit Router_A(config)#interface pppoe 1 Router_A(config-if pppoe 1)# ip address 192.0.2.1 Router_A(config-if pppoe 1)# ip nat inside source list 1 interface Router_A(config-if pppoe 1)# pppoe server test1 Router_A(config-if pppoe 1)# pppoe account ********@***.***.ne.jp ****** Router_A(config-if pppoe 1)# pppoe type lan Router_A(config-if pppoe 1)#exit Router_A(config)#crypto isakmp policy 1 Router_A(config-isakmp)# authentication prekey Router_A(config-isakmp)# encryption aes 256 Router_A(config-isakmp)# hash sha Router_A(config-isakmp)# key ascii furukawa Router_A(config-isakmp)# lifetime 86400 Router_A(config-isakmp)# my-identity kyoten1 Router_A(config-isakmp)# negotiation-mode aggressive Router_A(config-isakmp)# peer-identity address 192.0.2.129 Router_A(config-isakmp)#exit Router_A(config)#crypto map map1 1 Router_A(config-crypto-map)# match address 1 Router_A(config-crypto-map)# set peer address 192.0.2.129 Router_A(config-crypto-map)# set security-association lifetime seconds 28800 Router_A(config-crypto-map)# set transform-set t1 Router_A(config-crypto-map)# anti-replay disable Router_A(config-crypto-map)#exit Router_A(config)#class-map class1 Router_A(config-class-map)# match ip access-group 101 Router_A(config-class-map)#exit Router_A(config)#action-map action1 Router_A(config-action-map)# set queuing que1 Router_A(config-action-map)#exit Router_A(config)#class-map class2 Router_A(config-class-map)# match ip access-group 102 Router_A(config-class-map)#exit Router_A(config)#action-map action2 Router_A(config-action-map)# set queuing que2 Router_A(config-action-map)#exit Router_A(config)#policy-map policy1 Router_A(config-policy-map)# class class1 action action1 Router_A(config-policy-map)# class class2 action action2 Router_A(config-policy-map)#exit Router_A(config)# Router_A(config)#end Router_A# Router_A#save SIDE-A % saving working-config % finished saving Router_A#reset Going to reset with SIDE-A.frm and SIDE-A Boot-back not scheduled for next boot. Next rebooting firmware SIDE-A.frm is fine. Are you OK to cold start?(y/n)y |
※borrow設定について
親クラスに空きがあればその帯域を利用する設定です。設定帯域に抑制する場合はborrow設定を外してください。
Router B
| 設定内容 | 画面表示例 |
|---|---|
|
特権ユーザモードへの移行 パスワードの入力 設定情報の初期化 設定モードの変更 設定入力 設定保存 装置再起動 |
Router>enable Enter password: Router# Router#clear working.cfg Router# Router#configure terminal Router(config)#ip route 0.0.0.0 0.0.0.0 192.0.2.1 Router(config)#access-list 100 permit udp any any Router(config)#hostname Router_B Router(config)#ip route 172.16.0.0 255.255.0.0 connected ipsecif 1 Router(config)#access-list 101 permit tcp any any eq www Router(config)#access-list 102 permit tcp any any eq ftp Router(config)#access-list 102 permit tcp any any eq ftp-data Router(config)#vpn enable Router(config)#vpnlog enable Router(config)#ipsec access-list 1 ipsec ip 172.17.0.0 0.0.255.255 172.16.0.0 0.0.255.255 Router(config)#ipsec access-list 64 bypass ip any any Router(config)#ipsec transform-set t1 esp-null Router(config)#hostname Router_B Router_B(config)#interface pppoe 1 Router_B(config-if pppoe 1)# ip address 192.0.2.129 Router_B(config-if pppoe 1)# ip nat inside source list 1 interface Router_B(config-if pppoe 1)# pppoe server test1 Router_B(config-if pppoe 1)# pppoe account ********@***.***.ne.jp ****** Router_B(config-if pppoe 1)# pppoe type lan Router_B(config-if pppoe 1)#exit Router_B(config)#interface ipsecif 1 Router_B(config-if ipsecif 1)# qos output bandwidth 100M cbq Router_B(config-if ipsecif 1)# qos-que cbq default-que bandwidth 50 parent root-que borrow default※ Router_B(config-if ipsecif 1)# qos-que cbq root-que bandwidth 100 parent NULL Router_B(config-if ipsecif 1)# qos-que cbq que1 bandwidth 30 parent root-que priority 3 borrow※ Router_B(config-if ipsecif 1)# qos-que cbq que2 bandwidth 20 parent root-que priority 3 borrow※ Router_B(config-if ipsecif 1)# service-policy output policy1 Router_B(config-if ipsecif 1)# crypto map map1 Router_B(config-if ipsecif 1)#exit Router_B(config)#interface lan 1 Router_B(config-if lan 1)# ip address 172.17.0.2 255.255.255.0 Router_B(config-if lan 1)#exit Router_B(config)#crypto isakmp policy 1 Router_B(config-isakmp)# authentication prekey Router_B(config-isakmp)# encryption aes 256 Router_B(config-isakmp)# hash sha Router_B(config-isakmp)# key ascii furukawa Router_B(config-isakmp)# lifetime 86400 Router_B(config-isakmp)# nat-traversal enable Router_B(config-isakmp)# negotiation-mode main Router_B(config-isakmp)# peer-identity host kyoten1 Router_B(config-isakmp)#exit Router_B(config)#crypto map map1 1 Router_B(config-crypto-map)# match address 1 Router_B(config-crypto-map)# set peer host kyoten1 Router_B(config-crypto-map)# set security-association lifetime seconds 28800 Router_B(config-crypto-map)# set transform-set t1 Router_B(config-crypto-map)# anti-replay disable Router_B(config-crypto-map)#exit Router_B(config)#class-map class1 Router_B(config-class-map)# match ip access-group 101 Router_B(config-class-map)#exit Router_B(config)#action-map action1 Router_B(config-action-map)# set queuing que1 Router_B(config-action-map)#exit Router_B(config)#class-map class2 Router_B(config-class-map)# match ip access-group 102 Router_B(config-class-map)#exit Router_B(config)#action-map action2 Router_B(config-action-map)# set queuing que2 Router_B(config-action-map)#exit Router_B(config)#policy-map policy1 Router_B(config-policy-map)# class class1 action action1 Router_B(config-policy-map)# class class2 action action2 Router_B(config-policy-map)#exit Router_B(config)# Router_B(config)#end Router_B# Router_B#save SIDE-A % saving working-config % finished saving Router_B#reset Going to reset with SIDE-A.frm and SIDE-A Boot-back not scheduled for next boot. Next rebooting firmware SIDE-A.frm is fine. Are you OK to cold start?(y/n)y |
※borrow設定について
親クラスに空きがあればその帯域を利用する設定です。設定帯域に抑制する場合はborrow設定を外してください。
設定状態の確認 1
アクセスリストを確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
アクセスリスト情報を表示 設定が正しいことを確認 設定が正しいことを確認 |
Router_A#show access-lists Extended IP access list 101 permit tcp any any eq www log Extended IP access list 102 permit tcp any any eq ftp log permit tcp any any eq ftp-data log |
設定状態の確認 2
キューイング状況を確認します。
1.FTP通信のパケットは「que2」にキューイングされ、帯域は20Mbpsまで確保されます。
| 確認内容 | 画面表示例 |
|---|---|
|
キューの統計情報を表示 que2 のパケット数がカウントされていることを確認 |
Router_A#show qos queuing interface : ipsecif 1 queuing type : CBQ queuing-name : root-que (root que) priority : 0 queue length/limit : 0/50 sent/drop packets: packets : 18/0 bytes : 836/0 over count 0 delay count 0 queuing-name : default-que (default que) priority : 0 queue length/limit : 0/50 sent/drop packets: packets : 0/0 bytes : 0/0 over count 0 delay count 0 borrow : 0 queuing-name : que2 priority : 3 queue length/limit : 0/50 sent/drop packets: packets : 18/0 bytes : 836/0 over count 0 delay count 0 borrow : 0 queuing-name : que1 priority : 3 queue length/limit : 0/50 sent/drop packets: packets : 0/0 bytes : 0/0 over count 0 delay count 0 borrow : 0 |
2.WWW通信のパケットは「que1」にキューイングされ、帯域は30Mbpsまで確保されます。
| 確認内容 | 画面表示例 |
|---|---|
|
キューの統計情報を表示 que1 のパケット数がカウントされていることを確認 |
Router_A#show qos queuing interface : ipsecif 1 queuing type : CBQ queuing-name : root-que (root que) priority : 0 queue length/limit : 0/50 sent/drop packets: packets : 18/0 bytes : 836/0 over count 0 delay count 0 queuing-name : default-que (default que) priority : 0 queue length/limit : 0/50 sent/drop packets: packets : 0/0 bytes : 0/0 over count 0 delay count 0 borrow : 0 queuing-name : que2 priority : 3 queue length/limit : 0/50 sent/drop packets: packets : 18/0 bytes : 836/0 over count 0 delay count 0 borrow : 0 queuing-name : que1 priority : 3 queue length/limit : 0/50 sent/drop packets: packets : 35/0 bytes : 10329/0 over count 0 delay count 0 borrow : 0 |
All Rights Reserved, Copyright(C) FURUKAWA ELECTRIC CO., LTD. 2011
