設定例
VRRPで2台のルータを冗長し、VPNを冗長する設定
F60,F200,F2000
説明
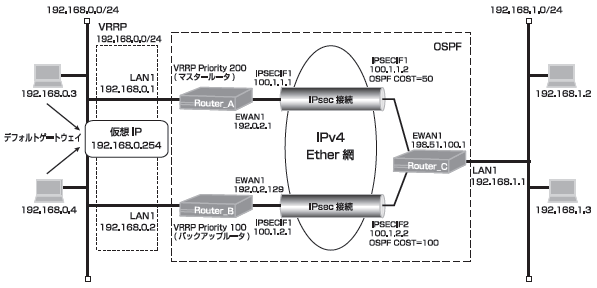
2台のルータのLAN側をVRRPでグループ化し、仮想アドレスを設定することにより、機器冗長することができます。
網側はIPSECで接続し、通信はIPSECトンネル経由で通信を行います。
マスタールータが正常な場合は、マスタールータと接続しているIPSECで通信が行われます。
マスタールータに故障が発生して通信できない状況になった場合、バックアップルータが仮想アドレスを引き継いでバックアップルータと接続しているIPSECで通信を再開します。
また、マスタールータの故障が復旧した場合は、マスタールータと接続しているIPSECで通信が切り戻る設定です。
Router_C側はOSPFによる経路切替を行います。
網側はIPSECで接続し、通信はIPSECトンネル経由で通信を行います。
マスタールータが正常な場合は、マスタールータと接続しているIPSECで通信が行われます。
マスタールータに故障が発生して通信できない状況になった場合、バックアップルータが仮想アドレスを引き継いでバックアップルータと接続しているIPSECで通信を再開します。
また、マスタールータの故障が復旧した場合は、マスタールータと接続しているIPSECで通信が切り戻る設定です。
Router_C側はOSPFによる経路切替を行います。
構成
コマンド設定
Router A
ip route 192.168.1.0 255.255.255.0 192.168.0.2 20 ip route 198.51.100.1 255.255.255.255 192.0.2.2 ip vrrp enable vpn enable vpnlog enable ipsec access-list 1 ipsec ip any any ipsec access-list 64 bypass ip any any ipsec transform-set aes256-sha esp-aes-256 esp-sha-hmac hostname Router_A interface ewan 1 ip mtu 1500 ip address 192.0.2.1 255.255.255.128 exit interface ipsecif 1 crypto map Router_C ip ospf network point-to-point ip address 100.1.1.1 255.255.255.0 ip mtu 1500 exit interface lan 1 ip address 192.168.0.1 255.255.255.0 vrrp 1 address 192.168.0.254 vrrp 1 priority 200 vrrp 1 preempt exit crypto isakmp policy 1 authentication prekey group 5 hash sha keepalive icmp always-send keepalive-icmp peer-address 192.168.1.1 keepalive-icmp source-interface lan 1 key ascii secret1 negotiation-mode main peer-identity address 198.51.100.1 exit crypto map Router_C 1 match address 1 set peer address 198.51.100.1 set pfs group5 set transform-set aes256-sha sa-up route interface ipsecif 1 10 exit router ospf network 100.1.1.0 0.0.0.255 area 0 redistribute connected metric-type 1 router-id 192.168.0.1 exit end
コマンド設定
Router B
ip route 192.168.1.0 255.255.255.0 connected ipsecif 1 ip route 198.51.100.1 255.255.255.255 192.0.2.130 ip vrrp enable vpn enable vpnlog enable ipsec access-list 1 ipsec ip any any ipsec access-list 64 bypass ip any any ipsec transform-set aes256-sha esp-aes-256 esp-sha-hmac hostname Router_B interface ewan 1 ip mtu 1500 ip address 192.0.2.129 255.255.255.128 exit interface ipsecif 1 crypto map Router_C ip ospf network point-to-point ip address 100.1.2.1 255.255.255.0 ip mtu 1500 exit interface lan 1 ip address 192.168.0.2 255.255.255.0 vrrp 1 address 192.168.0.254 vrrp 1 priority 100 exit crypto isakmp policy 1 authentication prekey group 5 hash sha key ascii secret1 negotiation-mode main peer-identity address 198.51.100.1 exit crypto map Router_C 1 match address 1 set peer address 198.51.100.1 set pfs group5 set transform-set aes256-sha exit router ospf network 100.1.2.0 0.0.0.255 area 0 redistribute connected metric-type 1 router-id 192.168.0.2 exit end
コマンド設定
Router C
ip route 192.0.2.1 255.255.255.255 198.51.100.2 ip route 192.0.2.129 255.255.255.255 198.51.100.2 ip route 192.168.0.1 255.255.255.255 connected ipsecif 1 ip route 192.168.0.2 255.255.255.255 connected ipsecif 2 vpn enable vpnlog enable ipsec access-list 1 ipsec ip any any ipsec access-list 2 ipsec ip any any ipsec access-list 64 bypass ip any any ipsec transform-set aes256-sha esp-aes-256 esp-sha-hmac hostname Router_C interface ewan 1 ip mtu 1500 ip address 198.51.100.1 255.255.255.0 exit interface ipsecif 1 crypto map Router_A ip ospf cost 50 ip ospf network point-to-point ip address 100.1.1.2 255.255.255.0 ip mtu 1500 exit interface ipsecif 2 crypto map Router_B ip ospf cost 100 ip ospf network point-to-point ip address 100.1.2.2 255.255.255.0 ip mtu 1500 exit interface lan 1 ip address 192.168.1.1 255.255.255.0 exit crypto isakmp policy 1 authentication prekey group 5 hash sha keepalive icmp always-send keepalive-icmp peer-address 192.168.0.1 keepalive-icmp source-interface lan 1 key ascii secret1 negotiation-mode main peer-identity address 192.0.2.1 exit crypto isakmp policy 2 authentication prekey group 5 hash sha keepalive icmp always-send keepalive-icmp peer-address 192.168.0.2 keepalive-icmp source-interface lan 1 key ascii secret1 negotiation-mode main peer-identity address 192.0.2.129 exit crypto map Router_A 1 match address 1 set peer address 192.0.2.1 set pfs group5 set security-association always-up set transform-set aes256-sha exit crypto map Router_B 2 match address 2 set peer address 192.0.2.129 set pfs group5 set security-association always-up set transform-set aes256-sha exit router ospf network 100.1.1.0 0.0.0.255 area 0 network 100.1.2.0 0.0.0.255 area 0 router-id 192.168.1.1 exit end
設定手順
Router A
マスタールータが復旧して、バックアップルータから切り替わる場合の動作を指定します。
"vrrp 1 preempt"
| 設定内容 | 画面表示例 |
|---|---|
|
特権ユーザモードへの移行 パスワードの入力 設定情報の初期化 設定モードの変更 設定入力 設定保存 装置再起動 |
Router>enable Enter password: Router# Router#clear working.cfg Router# Router#configure terminal Router(config)#ip route 192.168.1.0 255.255.255.0 192.168.0.2 20 Router(config)#ip route 198.51.100.1 255.255.255.255 192.0.2.2 Router(config)#ip vrrp enable Router(config)#vpn enable Router(config)#vpnlog enable Router(config)#ipsec access-list 1 ipsec ip any any Router(config)#ipsec access-list 64 bypass ip any any Router(config)#ipsec transform-set aes256-sha esp-aes-256 esp-sha-hmac Router(config)#hostname Router_A Router_A(config)#interface ewan 1 Router_A(config-if ewan 1)# ip mtu 1500 Router_A(config-if ewan 1)# ip address 192.0.2.1 255.255.255.128 Router_A(config-if ewan 1)#exit Router_A(config)#interface ipsecif 1 Router_A(config-if ipsecif 1)# crypto map Router_C Router_A(config-if ipsecif 1)# ip ospf network point-to-point Router_A(config-if ipsecif 1)# ip address 100.1.1.1 255.255.255.0 Router_A(config-if ipsecif 1)# ip mtu 1500 Router_A(config-if ipsecif 1)#exit Router_A(config)#interface lan 1 Router_A(config-if lan 1)# ip address 192.168.0.1 255.255.255.0 Router_A(config-if lan 1)# vrrp 1 address 192.168.0.254 Router_A(config-if lan 1)# vrrp 1 priority 200 Router_A(config-if lan 1)# vrrp 1 preempt Router_A(config-if lan 1)#exit Router_A(config)#crypto isakmp policy 1 Router_A(config-isakmp)# authentication prekey Router_A(config-isakmp)# group 5 Router_A(config-isakmp)# hash sha Router_A(config-isakmp)# keepalive icmp always-send Router_A(config-isakmp)# keepalive-icmp peer-address 192.168.1.1 Router_A(config-isakmp)# keepalive-icmp source-interface lan 1 Router_A(config-isakmp)# key ascii secret1 Router_A(config-isakmp)# negotiation-mode main Router_A(config-isakmp)# peer-identity address 198.51.100.1 Router_A(config-isakmp)#exit Router_A(config)#crypto map Router_C 1 Router_A(config-crypto-map)# match address 1 Router_A(config-crypto-map)# set peer address 198.51.100.1 Router_A(config-crypto-map)# set pfs group5 Router_A(config-crypto-map)# set transform-set aes256-sha Router_A(config-crypto-map)# sa-up route interface ipsecif 1 10 Router_A(config-crypto-map)#exit Router_A(config)#router ospf Router_A(config-ospf)# network 100.1.1.0 0.0.0.255 area 0 Router_A(config-ospf)# redistribute connected metric-type 1 Router_A(config-ospf)# router-id 192.168.0.1 Router_A(config-ospf)#exit Router_A(config)# Router_A(config)#end Router_A# Router_A#save SIDE-A % saving working-config % finished saving Router_A#reset Going to reset with SIDE-A.frm and SIDE-A.cfg. Boot-back not scheduled for next boot. Next rebooting firmware SIDE-A.frm is fine. Are you OK to cold start?(y/n)y |
設定手順
Router B
| 設定内容 | 画面表示例 |
|---|---|
|
特権ユーザモードへの移行 パスワードの入力 設定情報の初期化 設定モードの変更 設定入力 設定保存 装置再起動 |
Router>enable Enter password: Router# Router#clear working.cfg Router# Router#configure terminal Router(config)#ip route 192.168.1.0 255.255.255.0 connected ipsecif 1 Router(config)#ip route 198.51.100.1 255.255.255.255 192.0.2.130 Router(config)#ip vrrp enable Router(config)#vpn enable Router(config)#vpnlog enable Router(config)#ipsec access-list 1 ipsec ip any any Router(config)#ipsec access-list 64 bypass ip any any Router(config)#ipsec transform-set aes256-sha esp-aes-256 esp-sha-hmac Router(config)#hostname Router_B Router_B(config)#interface ewan 1 Router_B(config-if ewan 1)# ip mtu 1500 Router_B(config-if ewan 1)# ip address 192.0.2.129 255.255.255.128 Router_B(config-if ewan 1)#exit Router_B(config)#interface ipsecif 1 Router_B(config-if ipsecif 1)# crypto map Router_C Router_B(config-if ipsecif 1)# ip ospf network point-to-point Router_B(config-if ipsecif 1)# ip address 100.1.2.1 255.255.255.0 Router_B(config-if ipsecif 1)# ip mtu 1500 Router_B(config-if ipsecif 1)#exit Router_B(config)#interface lan 1 Router_B(config-if lan 1)# ip address 192.168.0.2 255.255.255.0 Router_B(config-if lan 1)# vrrp 1 address 192.168.0.254 Router_B(config-if lan 1)# vrrp 1 priority 100 Router_B(config-if lan 1)#exit Router_B(config)#crypto isakmp policy 1 Router_B(config-isakmp)# authentication prekey Router_B(config-isakmp)# group 5 Router_B(config-isakmp)# hash sha Router_B(config-isakmp)# key ascii secret1 Router_B(config-isakmp)# negotiation-mode main Router_B(config-isakmp)# peer-identity address 198.51.100.1 Router_B(config-isakmp)#exit Router_B(config)#crypto map Router_C 1 Router_B(config-crypto-map)# match address 1 Router_B(config-crypto-map)# set peer address 198.51.100.1 Router_B(config-crypto-map)# set pfs group5 Router_B(config-crypto-map)# set transform-set aes256-sha Router_B(config-crypto-map)#exit Router_B(config)#router ospf Router_B(config-ospf)# network 100.1.2.0 0.0.0.255 area 0 Router_B(config-ospf)# redistribute connected metric-type 1 Router_B(config-ospf)# router-id 192.168.0.2 Router_B(config-ospf)#exit Router_B(config)# Router_B(config)#end Router_B# Router_B#save SIDE-A % saving working-config % finished saving Router_B#reset Going to reset with SIDE-A.frm and SIDE-A.cfg. Boot-back not scheduled for next boot. Next rebooting firmware SIDE-A.frm is fine. Are you OK to cold start?(y/n)y |
設定手順
Router C
マスタールータ、バックアップルータから配信してくる経路情報を受け取るためにOSPFを設定をします。
| 設定内容 | 画面表示例 |
|---|---|
|
特権ユーザモードへの移行 パスワードの入力 設定情報の初期化 設定モードの変更 設定入力 設定保存 装置再起動 |
Router>enable Enter password: Router# Router#clear working.cfg Router# Router#configure terminal Router(config)#ip route 192.0.2.1 255.255.255.255 198.51.100.2 Router(config)#ip route 192.0.2.129 255.255.255.255 198.51.100.2 Router(config)#ip route 192.168.0.1 255.255.255.255 connected ipsecif 1 Router(config)#ip route 192.168.0.2 255.255.255.255 connected ipsecif 2 Router(config)#vpn enable Router(config)#vpnlog enable Router(config)#ipsec access-list 1 ipsec ip any any Router(config)#ipsec access-list 2 ipsec ip any any Router(config)#ipsec access-list 64 bypass ip any any Router(config)#ipsec transform-set aes256-sha esp-aes-256 esp-sha-hmac Router(config)#hostname Router_C Router_C(config)#interface ewan 1 Router_C(config-if ewan 1)# ip mtu 1500 Router_C(config-if ewan 1)# ip address 198.51.100.1 255.255.255.0 Router_C(config-if ewan 1)#exit Router_C(config)#interface ipsecif 1 Router_C(config-if ipsecif 1)# crypto map Router_A Router_C(config-if ipsecif 1)# ip ospf cost 50 Router_C(config-if ipsecif 1)# ip ospf network point-to-point Router_C(config-if ipsecif 1)# ip address 100.1.1.2 255.255.255.0 Router_C(config-if ipsecif 1)# ip mtu 1500 Router_C(config-if ipsecif 1)#exit Router_C(config)#interface ipsecif 2 Router_C(config-if ipsecif 2)# crypto map Router_B Router_C(config-if ipsecif 2)# ip ospf cost 100 Router_C(config-if ipsecif 2)# ip ospf network point-to-point Router_C(config-if ipsecif 2)# ip address 100.1.2.2 255.255.255.0 Router_C(config-if ipsecif 2)# ip mtu 1500 Router_C(config-if ipsecif 2)#exit Router_C(config)#interface lan 1 Router_C(config-if lan 1)# ip address 192.168.1.1 255.255.255.0 Router_C(config-if lan 1)#exit Router_C(config)#crypto isakmp policy 1 Router_C(config-isakmp)# authentication prekey Router_C(config-isakmp)# group 5 Router_C(config-isakmp)# hash sha Router_C(config-isakmp)# keepalive icmp always-send Router_C(config-isakmp)# keepalive-icmp peer-address 192.168.0.1 Router_C(config-isakmp)# keepalive-icmp source-interface lan 1 Router_C(config-isakmp)# key ascii secret1 Router_C(config-isakmp)# negotiation-mode main Router_C(config-isakmp)# peer-identity address 192.0.2.1 Router_C(config-isakmp)#exit Router_C(config)#crypto isakmp policy 2 Router_C(config-isakmp)# authentication prekey Router_C(config-isakmp)# group 5 Router_C(config-isakmp)# hash sha Router_C(config-isakmp)# keepalive icmp always-send Router_C(config-isakmp)# keepalive-icmp peer-address 192.168.0.2 Router_C(config-isakmp)# keepalive-icmp source-interface lan 1 Router_C(config-isakmp)# key ascii secret1 Router_C(config-isakmp)# negotiation-mode main Router_C(config-isakmp)# peer-identity address 192.0.2.129 Router_C(config-isakmp)#exit Router_C(config)#crypto map Router_A 1 Router_C(config-crypto-map)# match address 1 Router_C(config-crypto-map)# set peer address 192.0.2.1 Router_C(config-crypto-map)# set pfs group5 Router_C(config-crypto-map)# set security-association always-up Router_C(config-crypto-map)# set transform-set aes256-sha Router_C(config-crypto-map)#exit Router_C(config)#crypto map Router_B 2 Router_C(config-crypto-map)# match address 2 Router_C(config-crypto-map)# set peer address 192.0.2.129 Router_C(config-crypto-map)# set pfs group5 Router_C(config-crypto-map)# set security-association always-up Router_C(config-crypto-map)# set transform-set aes256-sha Router_C(config-crypto-map)#exit Router_C(config)#router ospf Router_C(config-ospf)# network 100.1.1.0 0.0.0.255 area 0 Router_C(config-ospf)# network 100.1.2.0 0.0.0.255 area 0 Router_C(config-ospf)# router-id 192.168.1.1 Router_C(config-ospf)#exit Router_C(config)# Router_C(config)#end Router_C# Router_C#save SIDE-A % saving working-config % finished saving Router_C#reset Going to reset with SIDE-A.frm and SIDE-A.cfg. Boot-back not scheduled for next boot. Next rebooting firmware SIDE-A.frm is fine. Are you OK to cold start?(y/n)y |
設定状態の確認 1
正常時の各ルータの状態を確認します。
マスタールータ(Router A)のVRRP状態を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
VRRP状態の確認 状態がMasterなことを確認 |
Router_A#show vrrp VRRP action enable lan 1 Vrid 1 Priority 200 (Current 200) Preempt mode “on” Advertisement interval 1 Local ip address is 192.168.0.1 Virtual router ip address is 192.168.0.254 Virtual MAC address is 00:00:5e:00:01:01 Authentication type is “auth-none” state: Master uptime(sec): 1541 become master count: 1 advertise receive: 0 error advertise receive: 0 |
バックアップルータ(Router B)のVRRP状態を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
VRRP状態の確認 状態がBackupなことを確認 |
Router_B#show vrrp VRRP action enable lan 1 Vrid 1 Priority 100 (Current 100) Preempt mode “off” Advertisement interval 1 Local ip address is 192.168.0.2 Virtual router ip address is 192.168.0.254 Virtual MAC address is 00:00:5e:00:01:01 Authentication type is “auth-none” state: Backup uptime(sec): ----- become master count: 0 advertise receive: 1571 error advertise receive: 0 |
Router Cの経路情報を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
ルーティング情報を表示 ※ |
Router_C#show ip route Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF B - BGP, I - IKE, U - SA-UP, D - REDUNDANCY, E - EventAction A - AutoConfig, > - selected route, * - FIB route, p - stale info. O 100.1.1.0/24 [110/50] is directly connected, IPSECIF1, 00:08:11 C> * 100.1.1.0/24 is directly connected, IPSECIF1 O 100.1.2.0/24 [110/100] is directly connected, IPSECIF2, 00:08:21 C> * 100.1.2.0/24 is directly connected, IPSECIF2 C> * 127.0.0.0/8 is directly connected, LOOP0 O> * 192.0.2.0/25 [110/70] via 100.1.1.1, IPSECIF1, 00:08:10 S> * 192.0.2.1/32 [1/0] via 198.51.100.2, EWAN1 O> * 192.0.2.128/25 [110/120] via 100.1.2.1, IPSECIF2, 00:08:10 S> * 192.0.2.129/32 [1/0] via 198.51.100.2, EWAN1 O> * 192.168.0.0/24 [110/70] via 100.1.1.1, IPSECIF1, 00:08:10 S> * 192.168.0.1/32 [0/0] is directly connected, IPSECIF1 S> * 192.168.0.2/32 [0/0] is directly connected, IPSECIF2 C> * 192.168.1.0/24 is directly connected, LAN C> * 198.51.100.0/24 is directly connected, EWAN1 |
※:OSPFで経路配布される192.168.0.0/24のネットワークアドレスのネクストホップが、マスタールータの IPアドレス(100.1.1.1)になっていることを確認してください。
設定状態の確認 2
マスタールータ(Router A)のLAN側で障害発生時の各ルータの状態を確認します。
マスタールータ(Router A)のVRRP状態を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
VRRP状態の確認 状態が初期状態になることを確認 |
Router_A#show vrrp VRRP action enable lan 1 Vrid 1 Priority 200 (Current 200) Preempt mode “on” Advertisement interval 1 Local ip address is 0.0.0.0 Virtual router ip address is 192.168.0.254 Virtual MAC address is 00:00:5e:00:01:01 Authentication type is “auth-none” state: Initialize uptime(sec): ----- become master count: 9 advertise receive: 6 error advertise receive: 0 |
バックアップルータ(Router B)のVRRP状態を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
VRRP状態の確認 状態がMasterになることを確認 |
Router_B#show vrrp VRRP action enable lan 1 Vrid 1 Priority 100 (Current 100) Preempt mode “off” Advertisement interval 1 Local ip address is 192.168.0.2 Virtual router ip address is 192.168.0.254 Virtual MAC address is 00:00:5e:00:01:01 Authentication type is “auth-none” state: Master uptime(sec): 46 become master count: 1 advertise receive: 1948 error advertise receive: 0 |
Router Cの経路情報を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
ルーティング情報を表示 ※ |
Router_C#show ip route Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF B - BGP, I - IKE, U - SA-UP, D - REDUNDANCY, E - EventAction A - AutoConfig, > - selected route, * - FIB route, p - stale info. O 100.1.1.0/24 [110/50] is directly connected, IPSECIF1, 00:00:41 C> * 100.1.1.0/24 is directly connected, IPSECIF1 O 100.1.2.0/24 [110/100] is directly connected, IPSECIF2, 00:15:04 C> * 100.1.2.0/24 is directly connected, IPSECIF2 C> * 127.0.0.0/8 is directly connected, LOOP0 O> * 192.0.2.0/25 [110/70] via 100.1.1.1, IPSECIF1, 00:00:40 S> * 192.0.2.1/32 [1/0] via 198.51.100.2, EWAN1 O> * 192.0.2.128/25 [110/120] via 100.1.2.1, IPSECIF2, 00:14:53 S> * 192.0.2.129/32 [1/0] via 198.51.100.2, EWAN1 O> * 192.168.0.0/24 [110/120] via 100.1.2.1, IPSECIF2, 00:00:50 S> * 192.168.0.1/32 [0/0] is directly connected, IPSECIF1 S> * 192.168.0.2/32 [0/0] is directly connected, IPSECIF2 C> * 192.168.1.0/24 is directly connected, LAN C> * 198.51.100.0/24 is directly connected, EWAN |
※:OSPFで経路配布される192.168.0.0/24のネットワークアドレスのネクストホップが、バックアップルータ のIPアドレス(100.1.2.1)になっていることを確認します。
設定状態の確認 3
マスタールータ(Router A)のLAN側障害からの復旧時の状態を確認します。
マスタールータ(Router A)のVRRP状態を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
VRRP状態の確認 状態がMasterになったことを確認 |
Router_A#show vrrp VRRP action enable lan 1 Vrid 1 Priority 200 (Current 200) Preempt mode “on” Advertisement interval 1 Local ip address is 192.168.0.1 Virtual router ip address is 192.168.0.254 Virtual MAC address is 00:00:5e:00:01:01 Authentication type is “auth-none” state: Master uptime(sec): 53 become master count: 2 advertise receive: 39 error advertise receive: 0 |
バックアップルータ(Router B)のVRRP状態を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
VRRP状態の確認 状態がBackupになったことを確認 |
Router_B#show vrrp VRRP action enable lan 1 Vrid 1 Priority 100 (Current 100) Preempt mode “on” Advertisement interval 1 Local ip address is 192.168.0.2 Virtual router ip address is 192.168.0.254 Virtual MAC address is 00:00:5e:00:01:01 Authentication type is “auth-none” state: Backup uptime(sec): ----- become master count: 1 advertise receive: 2005 error advertise receive: 0 |
Router Cの経路情報を確認します。
| 確認内容 | 画面表示例 |
|---|---|
|
ルーティング情報を表示 ※ |
Router_C#show ip route Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF B - BGP, I - IKE, U - SA-UP, D - REDUNDANCY, E - EventAction A - AutoConfig, > - selected route, * - FIB route, p - stale info. O 100.1.1.0/24 [110/50] is directly connected, IPSECIF1, 00:00:51 C> * 100.1.1.0/24 is directly connected, IPSECIF1 O 100.1.2.0/24 [110/100] is directly connected, IPSECIF2, 00:22:13 C> * 100.1.2.0/24 is directly connected, IPSECIF2 C> * 127.0.0.0/8 is directly connected, LOOP0 O> * 192.0.2.0/25 [110/70] via 100.1.1.1, IPSECIF1, 00:00:50 S> * 192.0.2.1/32 [1/0] via 198.51.100.2, EWAN1 O> * 192.0.2.128/25 [110/120] via 100.1.2.1, IPSECIF2, 00:22:02 S> * 192.0.2.129/32 [1/0] via 198.51.100.2, EWAN1 O> * 192.168.0.0/24 [110/70] via 100.1.1.1, IPSECIF1, 00:00:50 S> * 192.168.0.1/32 [0/0] is directly connected, IPSECIF1 S> * 192.168.0.2/32 [0/0] is directly connected, IPSECIF2 C> * 192.168.1.0/24 is directly connected, LAN C> * 198.51.100.0/24 is directly connected, EWAN1 |
※:OSPFで経路配布される192.168.0.0/24のネットワークアドレスのネクストホップが、マスタールータの IPアドレス(100.1.1.1)になっていることを確認します。
All Rights Reserved, Copyright(C) FURUKAWA ELECTRIC CO., LTD. 2012
